When you register a third-party application in your tenant, a service principal is created in your Azure AD to represent it. That service principal is used to define the permissions granted to the application as well the permissions to manage the app itself in the tenant.
As a common practice, an application vendor defines all the permissions the app requires to function correctly, and you grant consent for those permissions while registering the app in a tenant. In some cases, e.g., working in regulated industries or environments with high security requirements, you might need to reduce the list of permissions requested during the app registration to specific ones only.
In this blog post, I will share some tips on how you can update the OAuth2 permission grants for an existing application (a service principal if being technically precise) in your tenant.
Please note that changing (revoking) OAuth2 permission grants for an app might impact its functionality. If you are to modify permissions to a third-party application, make sure to consult with its vendor first.
Problem statement
Suppose you explore the options available to you to review application permissions on the Azure portal. In that case, you might notice that most of them allow only removing all OAuth2 permission grants at once. The sample PowerShell script provided by Microsoft uses the AzureAD cmdlets that don’t have an option to modify the existing grants:
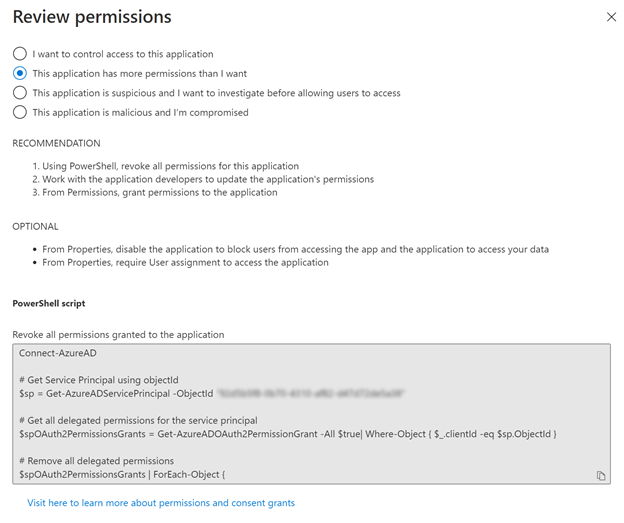
The recently updated Update-AzADServicePrincipalcmdlet uses Microsoft Graph API and doesn’t have sufficient documentation on constructing input parameters to make it work properly. The same lack of documentation affects the Update-MgOauth2PermissionGrant cmdlet from the Microsoft Graph PowerShell SDK, making using it quite problematic too. My attempts to use ‘Microsoft.Graph’ cmdlets ended up with an error stating that the scope property defining the grants is read-only and cannot be updated.
Using the Azure CLI for the task doesn’t help either, as it can create new grants but not modify the existing ones.
Solution
After unsuccessful attempts to use the Azure Portal, Azure PowerShell, Microsoft Graph PowerShell SDK and Azure CLI for updating the OAuth2 permission grants, the only option left was to work with the Microsoft Graph REST API that provides an endpoint for updating the delegated permission grants.
The resulting execution sequence to update the OAuth2 permission grants for an Azure AD service principal will be the following:
- Go to Graph Explorer and log in with the admin account for your tenant. Consent for the 'Directory.ReadWrite.All' permissions.
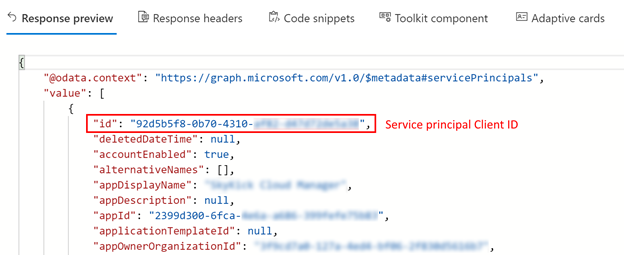
- Search for the Client ID of the service principal you want to update the grants to:
GET https://graph.microsoft.com/v1.0/servicePrincipals?$search="displayName:your_app_name"
Pay attention to the ConsistencyLevel header that must be set to ‘eventual.’
- Search for the OAuth2 permission grants by the Client ID you identified:
GET https://graph.microsoft.com/v1.0/oauth2PermissionGrants
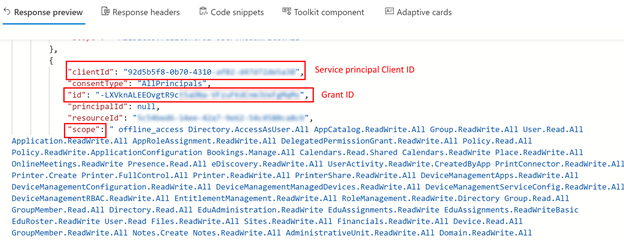
- [Optional] Get the specific grant only
GET https://graph.microsoft.com/v1.0/oauth2PermissionGrants/{id}
Where ID is the unique identifier of the grant and NOT the Client ID of your app. It has a format different from the common GUID-like identifiers. - Update the required grant with a new scope by using the PATCH method:
PATCH https://graph.microsoft.com/v1.0/oauth2PermissionGrants/{id}
and providing a request body in the following format:
{ "scope": " offline_access Directory.AccessAsUser.All Directory.Read.All Group.ReadWrite.All Group.Read.All GroupMember.Read.All GroupMember.ReadWrite.All User.Read.All User.Read" }
The scope property of the request must enumerate the complete list of granted permissions separated by spaces. - [Optional] Verify that the OAuth2 permission grant was updated with the scope provided earlier:
GET https://graph.microsoft.com/v1.0/oauth2PermissionGrants/{id}
Additionally, you can check that the Azure portal displays the updated app permissions too.
I hope that workaround will be helpful for anyone looking to modify existing app permissions without completely revoking them or deleting the app registration.
If you want to get recent updates to my blog, please subscribe with your email using the form below 👇
P.S. You will need to confirm your subscription by email to avoid unwanted spam to other people's mailboxes.
Member discussion: